Lockbit: Investigators claim to have uncovered the head of the ransomware gang
Australian, British and US authorities impose sanctions on a suspect and pay a million-euro reward for information.
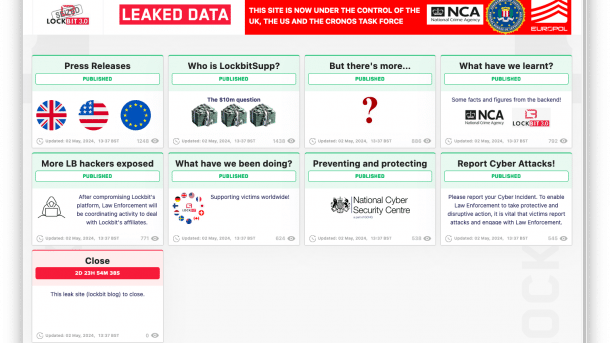
Counter-attack: Law enforcement officials have unmasked the man behind the LockBit gang and are now presenting wanted notices on his own leak site.
(Bild: Screenshot / heise Security)
An international consortium of law enforcement agencies – including the German BKA and the LKA Schleswig-Holstein – has determined the identity of the LockBit ringleader. According to this, a Russian citizen by the name of Dmitry K is behind the pseudonym "LockBitSupp". This was announced on Tuesday by the US Treasury Department and the British National Crime Agency (NCA), among others.
The 31-year-old suspect is said to live in Voronesh (Воронеж), Russia, a good 500 kilometers south of Moscow. As the developer of the ransomware-as-a-service (RaaS) service "LockBit 3.0", he is said to have collected 20 percent of all ransoms and allegedly earned over 100 million dollars. The US State Department has offered a reward of 10 million US dollars for information leading to his capture; the USA is also bringing charges against the man.
If he has invested any of these assets in the USA, Australia or Great Britain, K. will now have to forfeit them: All three countries have imposed sanctions on the Russian and are freezing his assets to the extent that they can get hold of them. However, as LockBitSupp usually had its share of the ransom paid out in Bitcoin, there is probably not much to be gained.
The majority of LockBit affiliates came away empty-handed
The majority of the LockBit gang leader's criminal henchmen did not make much money either: almost 60 percent of the so-called "affiliates" did not earn a cent from the ransomware. As the investigators found out, only 80 of the total of 194 affiliates brought a ransom negotiation to a successful conclusion, with the remaining 114 coming away empty-handed. As each newly recruited LockBit henchman had to pay a deposit of one Bitcoin, each of the unsuccessful would-be extortionists made a loss of up to 75,000 US dollars. Only the head of the gang who collected the pledge made a profit.
(Bild: UK National Crime Agency)
As expected, neither his employees nor his victims were very principled: the investigators of the Cronos working group found various examples of malfunctioning decryption routines, which were only acknowledged by "Lockbit Support" with a shrug of the shoulders. After the allegedly unauthorized attack on a children's hospital, the affiliate responsible was not dismissed, but was allowed to continue working with the Lockbit ransomware even after the attack. In addition, the decryption software provided free of charge as part of an apology did not work properly.
The investigators have identified a total of 3811 victims of the ransomware gang and helped them – where possible – to restore their data. Since February, they have also recorded a sharp increase in the number of hits on the "NoMoreRansom.org" website, which, according to the authorities, can now decrypt over 150 types of ransomware.
It remains to be seen whether LockBitSupp, which was quoted on X with pithy remarks just a few days ago, will comment on the sanctions and its supposed exposure. Yesterday alone, more than fifty new entries appeared on the ransomware group's darknet leak site, many of which were merely given a new date, presumably to feign activity.
(cku)